Single sign-on (SSO) has made life easier for a lot of folks out there. By allowing users to log in using a single ID across multiple related but independent systems, this reduces password fatigue and makes logging in to multiple accounts at the same time relatively easy. The flip side of this increased convenience is that users have gotten accustomed to popup windows asking for their credentials. Browser in the browser (BitB) attacks leverage this established comfort by simulating another browser window within the malicious page, which can be made nearly impossible to distinguish from the real deal.
Background
Many of us still remember what the Internet browsing experience of the late 1990’s was like. You would open an unfamiliar website and suddenly your browser window would be filled with a swarm of pop-up ads. Users quickly grew tired of this intrusive marketing technique, and the early 2000’s saw the emergence of pop-up and ad blockers as browser extensions. A lot of websites started incorporating these features as well; gone were the days of having to close a dozen little ads.
But, as is the way of the world, what was once old is new again. Pop-ups are back, this time serving a different purpose as the gateways to SSO (or single sign-on) log-ins. Single-sign on allows users to securely authenticate with multiple applications and websites using a single set of credentials. When logging in to an application or a website you are asked to create a new separate account for that service, or you can opt to use your existing credentials from a different service, such as Google or Facebook, to log in. As shown in the example below, choosing to use SSO causes a pop-up browser window to appear, asking for your username and password from a different service... the two most prominent examples being Google, Facebook, and sometimes Apple. In the example below, Facebook is being used as the gateway to Canva.
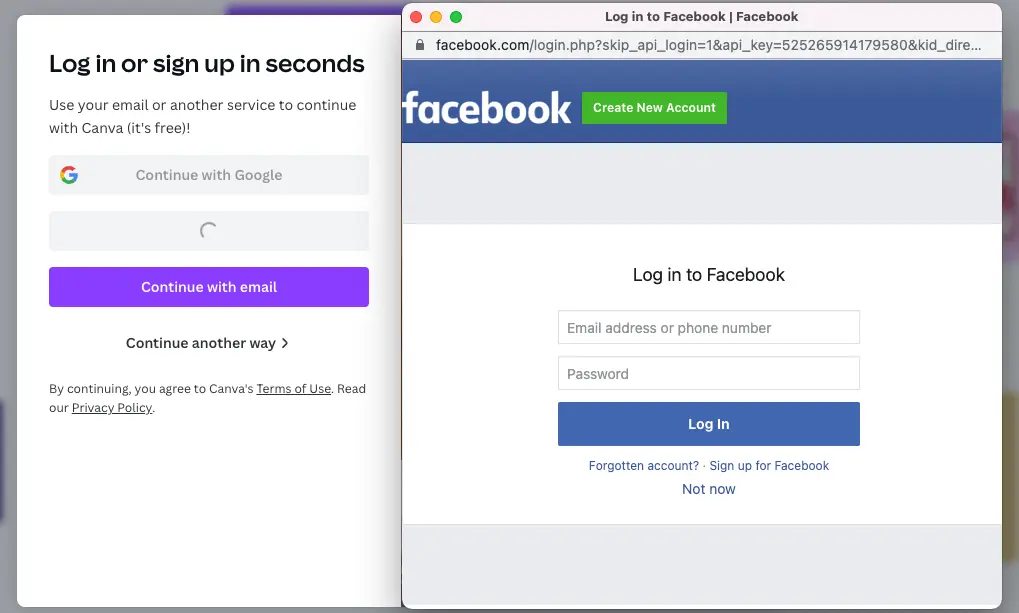
The attack
Some of you will already have realised the danger this introduces to unsuspecting users. While attackers can copy the contents of a legitimate website to make their malicious site look legitimate, inspecting the URL will, in most cases, reveal the site to be fraudulent (We've previously written on this topic here — Ed). With the pop-up login window, however, attackers have full control over all the elements within it. The URL can be spoofed to look exactly akin to a legitimate service. Technically, this technique is not too difficult to execute either. The attacker only needs to write a few lines of Javascript to make the pop-up window appear on top of the malicious website. Some more code and the window can be made draggable, and respond to the browser theme as well.
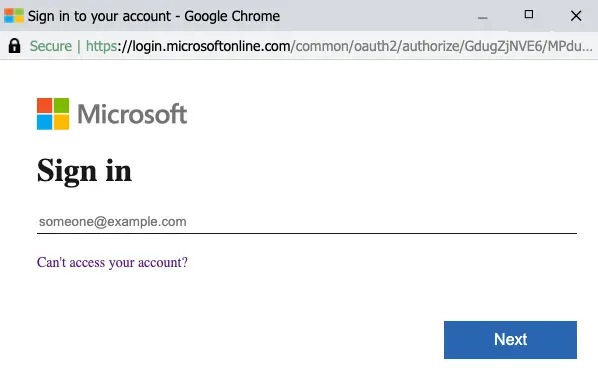

This fake pop-up login page can then include all the usual credential harvesting tricks used by attackers, such as asking for the password multiple times in the hopes of getting several passwords for the same user. When the credentials are finally accepted, the user might even be redirected to a legitimate website to diminish suspicion.
So how can a user tell the pop-up login window they’re being presented is fake? One way is by checking the URL of the underlying website, something few will realise to do as they will likely focus on the URL presented in the pop-up window instead. A quick and easy way to tell that the pop-up window is fake is to try dragging the pop-up outside the browser window: a fake pop-up window will stop at the border of the browser window, while a legitimate login pop-up can be moved outside these borders.
Staying off the hook
- Of course, all of the above is conditional on the attacker first luring the user to a malicious website. The best defence is being able to recognise such attempts and refraining from following that suspicious URL.
- If you do end up on a suspicious website with a pop-up asking for your credentials, don’t focus only on the pop-up, even if it looks completely legitimate. Look at the URL of the underlying webpage as well.
- Try dragging the pop-up login window both inside and outside the browser window. A fake pop-up will not be able to go outside the browser window. This takes minimum effort and can easily be incorporated to your everyday browsing routines.
- Subscribe to All Things Human Risk to get a monthly round up of our latest content
- Request a demo for a customized walkthrough of Hoxhunt







